How I almost got pwned by a Python Supply Chain Attack on Github
Recently, as part of a school project, I needed to find techniques to bypass Windows Defender with the help of the Python language.
So I did what I do best: going to Google and find some resources !
During my researches, I came accross a pretty explicit repository on Github named pycrypt :

This repository claims to to make any Python script undetectable by the Windows AV. So I decided to give it a try but first, I quickly checked the code and saw that it tried to launch a very weird library :

Looking at the commits, it seems that the famous package colorama, which is used to render a colored output for Python scripts was modified to this weird package named colourema :

Let’s check this package in detail on PyPi :

Looking at the author of the package, we can see several informations.
- Its account was created at the beginning of december
- He has only one package, colourema, which was created on December 29, 2022
- He is usurping the name of the real creator of colorama (tartley)

Okay, this looks really weird. Let’s download the library for further analysis :

After inspecting manually each script of the archive, the initalise.py one caught my attention :

If we inspect the code, we can see that a fonction named deinit() is declared and contains obfuscated code :

And of course, this function is called in the pycrypt.py code, at line 46 🤡 :
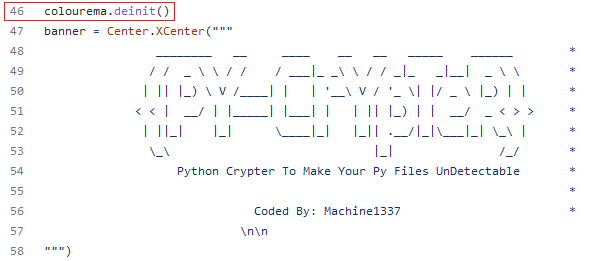
The last line of the function, with the eval() method, executes the deobfuscated code :

To deobfuscate the code automatically, I simply modified the function like this and put it in a file named deobf.py :

When I launched the script, I got this output :

Let’s check the content of file.py with a better view :

It starts to smell really bad 🤡 I then dug deeper by downloading at the Dropbox URL the mozila.sh file and it seems that it does more shady stuff :

We now have another Dropbox URL. Let’s check what this update file is :

Since I am awful at reversing, (especially on stripped Go binaries lol), I decided to upload it in Virustotal and got 6 matches :

The result speaks for itself, let’s ask to the judge the verdict :

With all the informations that we have, we then can conclude that :
- this is a Supply Chain Attack coming from the malicious Python package colourema.
- its purpose is probably to infect Kali Linux or Metasploit users, since it pretends to be a metasploit update.
- if I didn’t read the code, I probably would have been pwned.
Moral of the story :
Always read carefully the imports when you want to use an open-source tool !
I reported the issue to GitHub and currently wait for their actions.
Up : they did nothing 🤡
Thanks for reading,





